Cyber security is a key stage in any project involving connected equipment. IT departments and CISOs need to be reassured from the earliest stages of the project, because they are the guarantors of the integrity of information systems and data protection. As the GR100 is an autonomous, connected robot, it’s only natural that cyber security should raise questions. Here’s how to anticipate the expectations of IT Departments and demonstrate that the GR100 robot and its RB-OC* interface meet stringent IT security requirements.
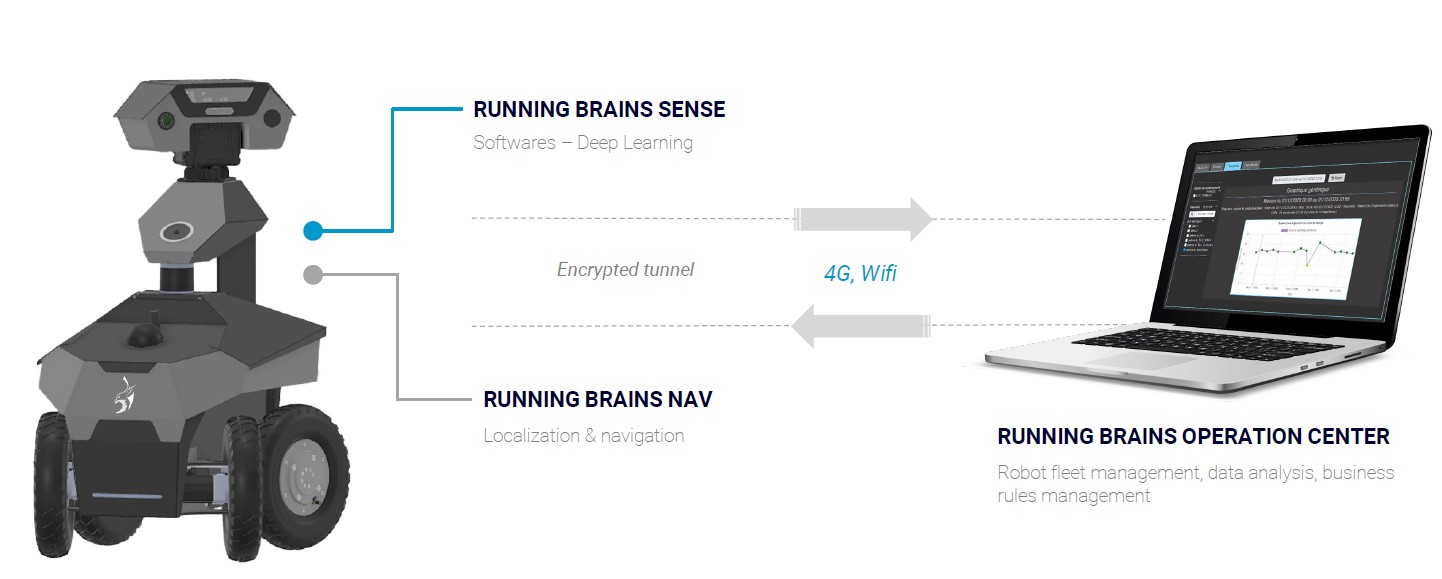
The rondier robot collects information from its sensors (video, thermal, anomaly detection, various sensors), which is then centralised on a secure cloud interface, the Running Brains Operations Center.
Today, our robots are deployed at many strategic sites such as nuclear power stations and airports. As a result, we are well aware of the requirements expected by our customers in terms of cybersecurity and compliance with RGPD rules. That’s why our team takes action every day to meet these requirements.
Here are the main points to emphasise to cybersecurity teams:
Data management, storage, transfer & AI
Data is managed in-house and stored on a server located in France (Ikoula ISO 27001 certified).
We create and use our own artificial intelligence algorithms. So we don't outsource images.
Compliance with the rules and provision of an RGPD charter on request.
Implementation of backup and restore management procedures (compliance with rules 1-2-3).
In addition, 2 servers are available to ensure rapid recovery.
Data flows are encrypted by default during storage and transfer between the robot and the RB-OC web interface.
RB-OC*: designed to meet the requirements of strategic sites
Access to the interface is subject to strong authentication (MFA) and managed by granular rights.
All logs, connections and actions are traced and time-stamped in the RB-OC interface.
It is possible to define different levels of access depending on the user's functions
Cybersecurity audit & ISO
Every year, our company is audited by an independent French body.
Our customers are authorised to audit us as long as they respect a schedule and make the audit report available to us for sharing.
We have launched an ISO 27001 certification procedure
Access to the GR100 robot
Via the RB-OC* web interface, via on-board WiFi (deactivated by default, can only be activated on the RB-OC*) and via the controller paired with the robot.
Aware of the challenges involved in installing a new technology such as the GR100 surveillance robot, we offer our customers a pre-signature scoping meeting with our cyber security department (RSSI). A Security Assurance Plan (SAP) can then be provided on request. This meeting enables us to answer any questions you may have about cyber security before the robot is deployed on site.
On the strength of our various customer experiences, we have had the opportunity to talk to the cyber departments of Storengy, EDF and Saipol before and after signing the contract. These meetings have enabled us to consolidate our knowledge and best practices and to put in place other security procedures to better meet the growing needs of our customers.
In addition, we train all our new employees in cybersecurity and regularly run awareness-raising campaigns among our staff.
Cyber security is no longer an option: it’s a prerequisite for success. By anticipating CIOs’ concerns and providing concrete, documented answers, you’ll make it easier for them to get behind the project to deploy a GR100 security robot.
You can also rely on Running Brains Robotics‘ transparency when it comes to data management, the audits it carries out and the technical support it provides to establish a climate of trust, which is essential for a smooth and secure deployment.
You now have all the tools you need to reassure your cybersecurity department!
* Running Brains Operations Center web interface

CMO at Running Brains Robotics